Add latest changes from gitlab-org/gitlab@master
Showing
22.0 KB
10.3 KB
48.6 KB
28.3 KB
29.6 KB
lib/api/entities/event.rb
0 → 100644
lib/api/entities/todo.rb
0 → 100644
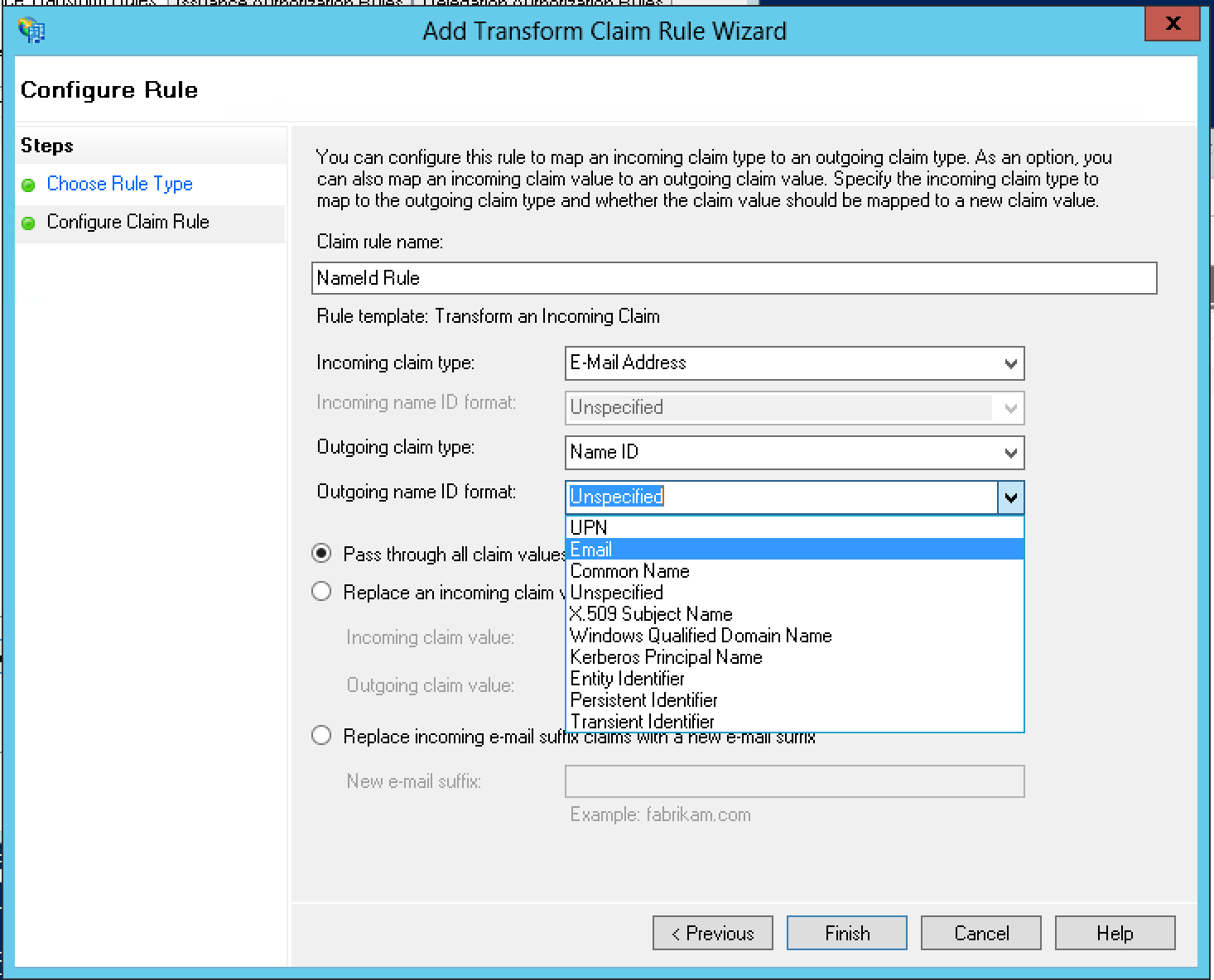
22.0 KB
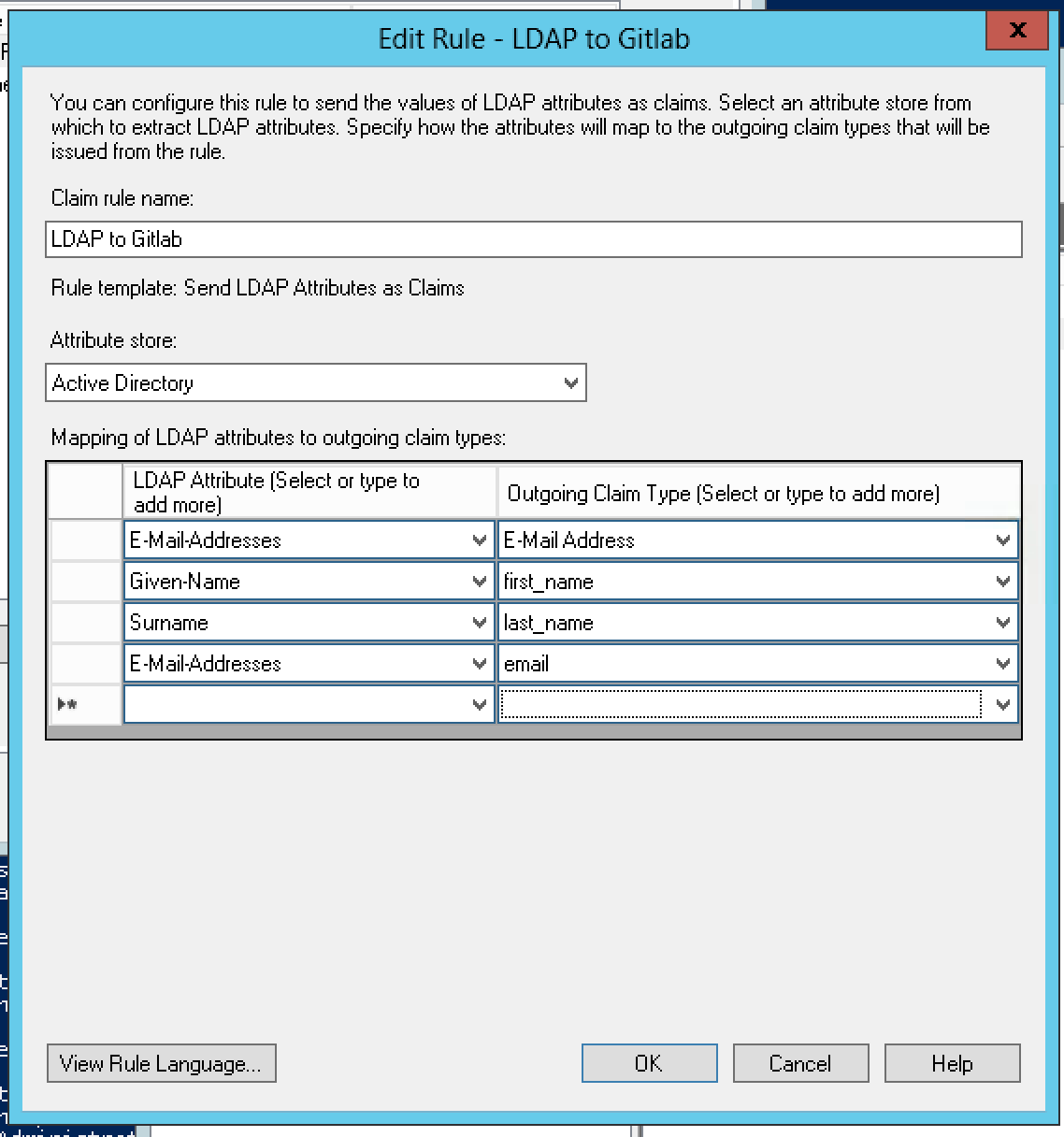
10.3 KB
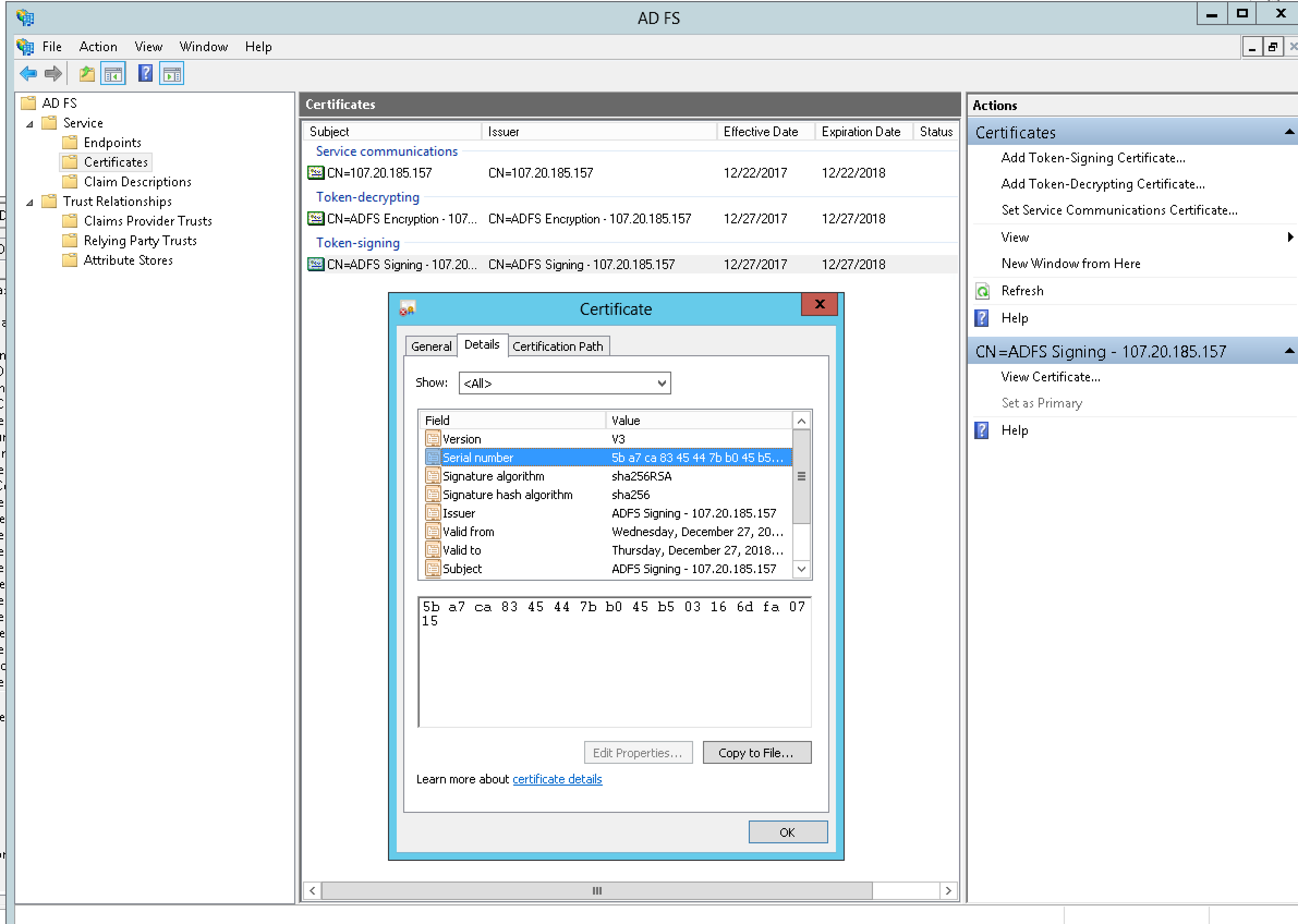
48.6 KB
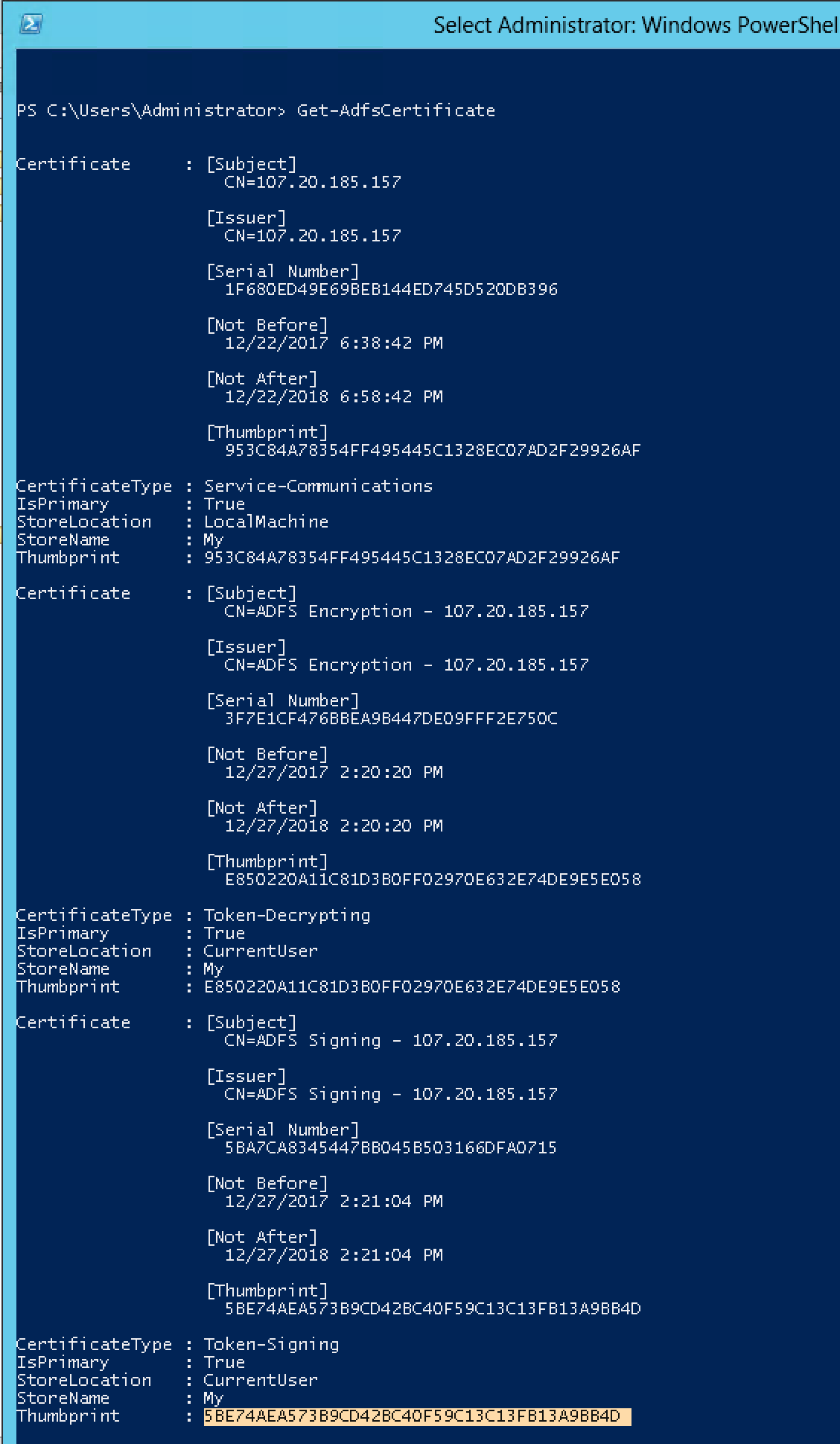
28.3 KB
29.6 KB
