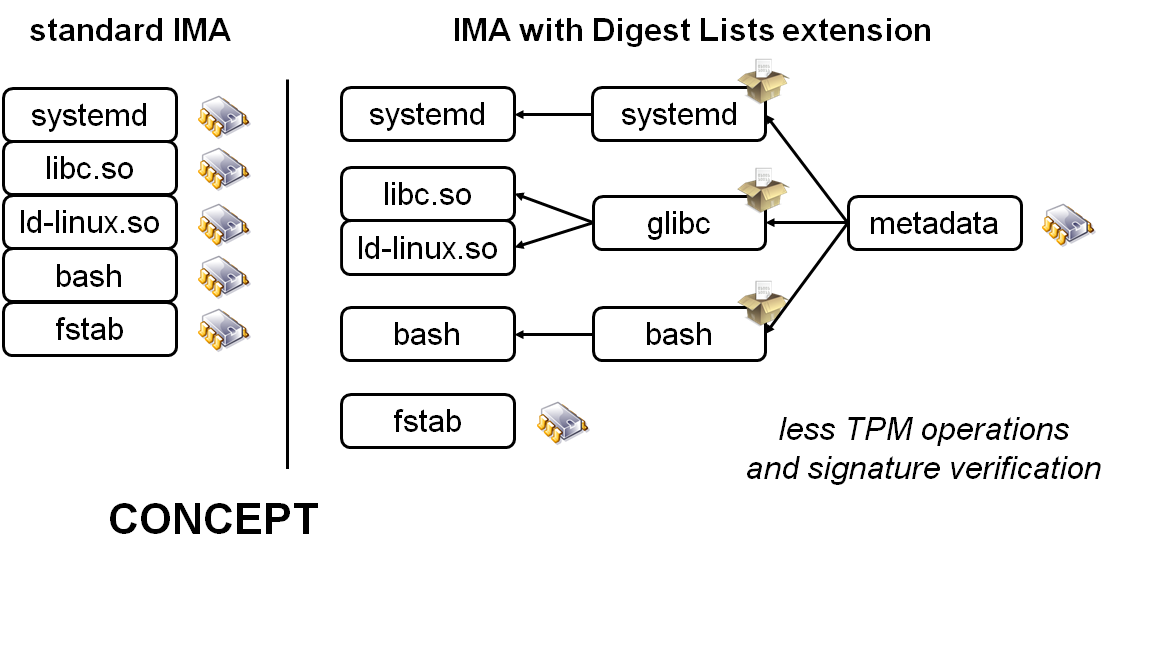
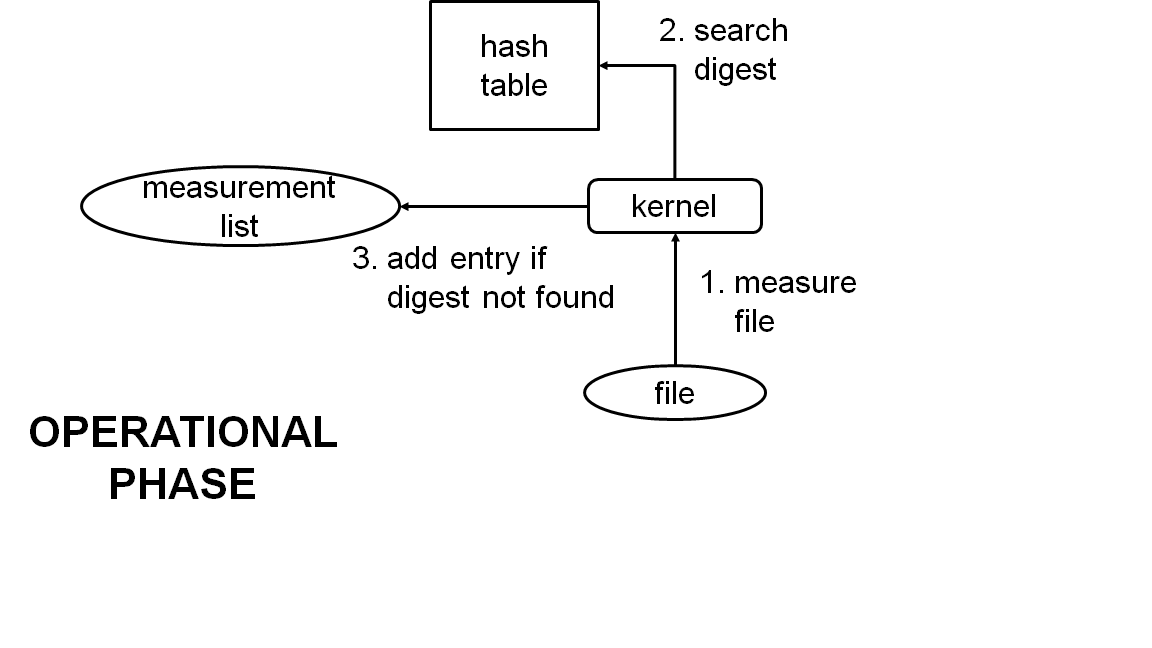
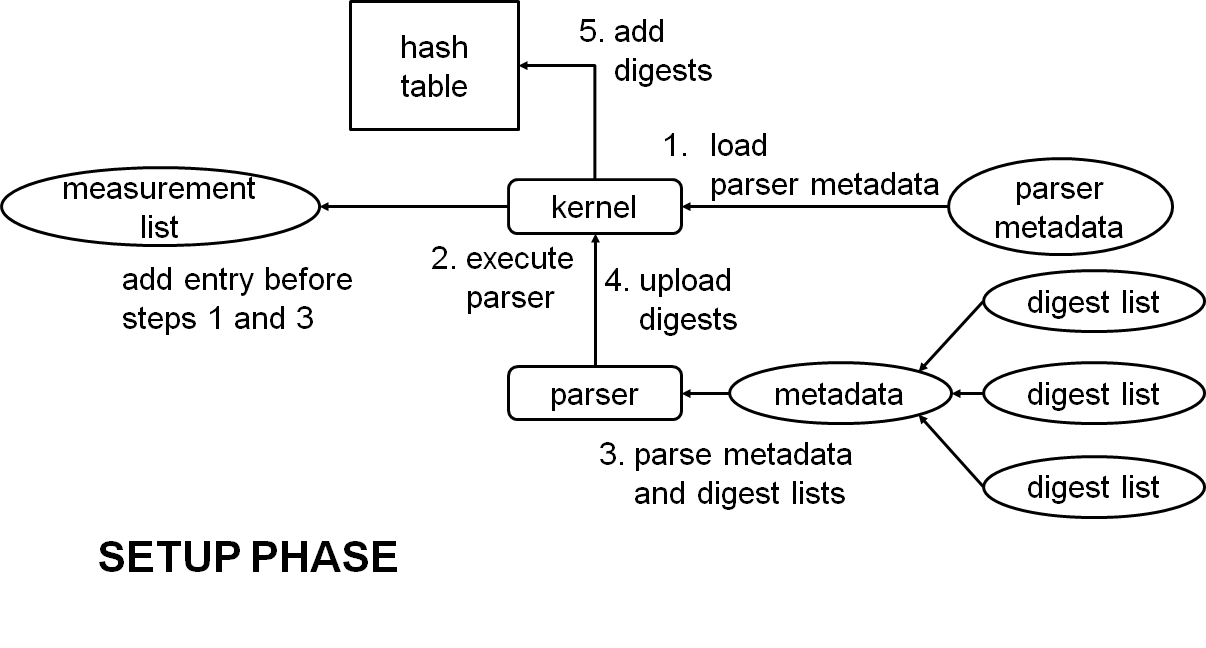
Update to version v0.3
Showing
此差异已折叠。
docs/digest_list_concept.png
已删除
100644 → 0
81.7 KB
27.1 KB
48.3 KB
docs/gen_parser_metadata.txt
已删除
100644 → 0
docs/modify_digest_lists.txt
已删除
100644 → 0
generators/Makefile.am
0 → 100644
generators/compact.c
0 → 100644
generators/copy.c
0 → 100644
generators/ima.c
0 → 100644
include/crypto.h
0 → 100644
include/deb.h
已删除
100644 → 0
include/kernel_ima.h
已删除
100644 → 0
include/list.h
0 → 100644
include/metadata.h
已删除
100644 → 0
include/pgp.h
已删除
100644 → 0
include/rpm.h
已删除
100644 → 0
include/securityfs.h
已删除
100644 → 0
include/xattr.h
0 → 100644
initrd/dracut/digestlist.conf
0 → 100644
lib/compact_list.c
0 → 100644
lib/crypto.c
0 → 100644
lib/generators/compact_list.c
已删除
100644 → 0
lib/generators/deb.c
已删除
100644 → 0
lib/kernel_ima.c
已删除
100644 → 0
此差异已折叠。
此差异已折叠。
lib/metadata.c
已删除
100644 → 0
此差异已折叠。
lib/parsers/deb.c
已删除
100644 → 0
此差异已折叠。
lib/pgp.c
已删除
100644 → 0
此差异已折叠。
lib/securityfs.c
已删除
100644 → 0
此差异已折叠。
lib/xattr.c
0 → 100644
此差异已折叠。
parsers/Makefile.am
0 → 100644
此差异已折叠。
parsers/ima.c
0 → 100644
此差异已折叠。
此差异已折叠。
scripts/xattr.awk
0 → 100644
此差异已折叠。
此差异已折叠。
src/gen_parser_metadata.c
已删除
100644 → 0
此差异已折叠。
src/modify_digest_lists.c
已删除
100644 → 0
此差异已折叠。
systemd/Makefile.am
0 → 100644
此差异已折叠。
文件已添加
tests/Makefile.am
0 → 100644
此差异已折叠。
tests/gen.c
0 → 100644
此差异已折叠。
tests/ima.c
0 → 100644
此差异已折叠。
tests/lib.c
0 → 100644
此差异已折叠。
tests/rpm.c
0 → 100644
此差异已折叠。