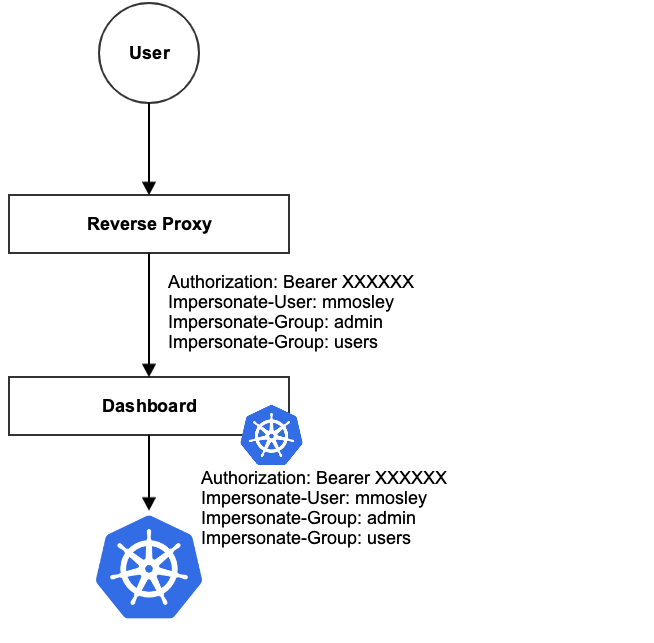
impersonation support for the dashboard (#4082)
* Added user impersonation and username to ui * groups working * Added unit tests, extras for impersonation * added docs * fixed formatting to be consistent * updates per pr review * ran npm frontend:fix per travis ci
Showing
52.4 KB